When trading cryptocurrencies over-the-counter (OTC), security is paramount. These high-value transactions involve sensitive data like private keys, KYC documents, and transaction records, making them attractive targets for cyberattacks. Without proper safeguards, you risk financial losses, identity theft, and regulatory penalties.
Here’s how to protect your assets during OTC trades:
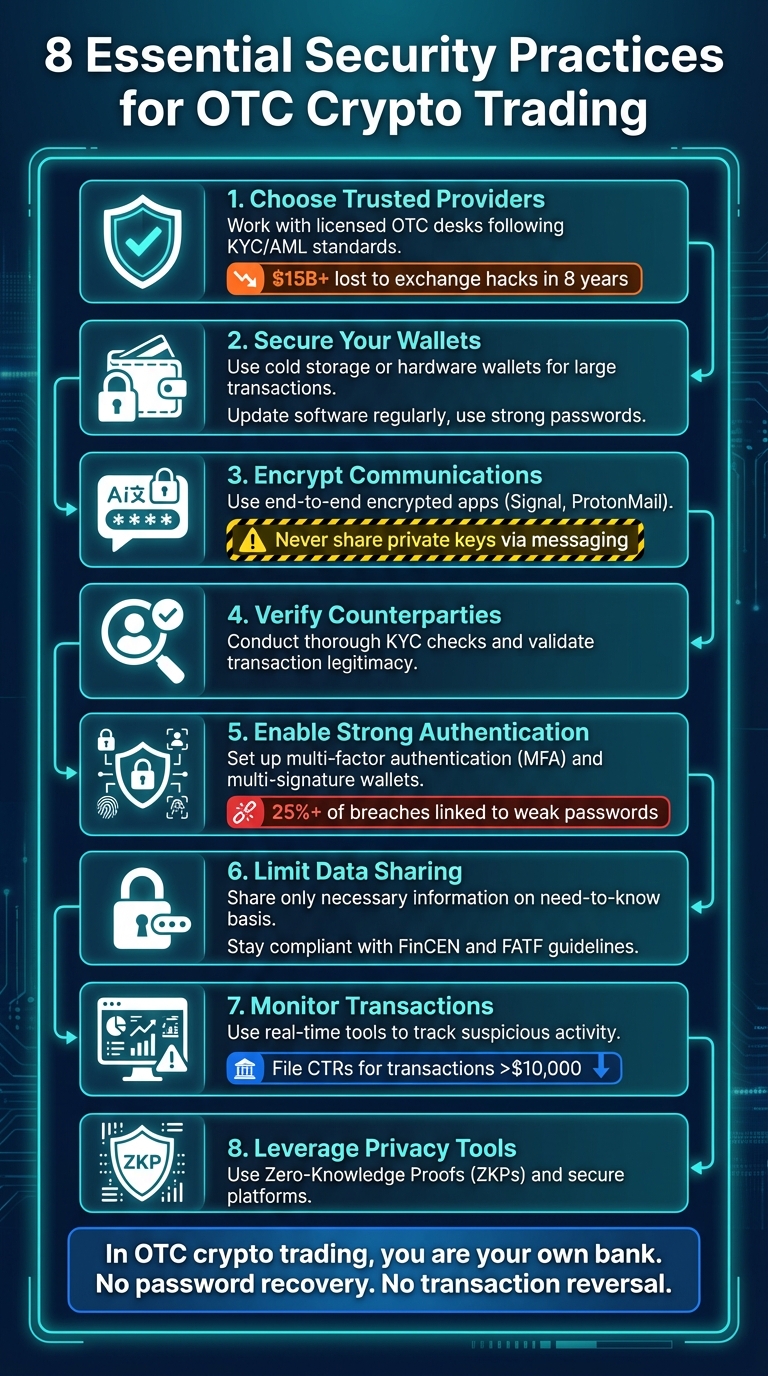
- Choose Trusted Providers: Work with licensed OTC desks that follow strict KYC/AML standards and use escrow or custodial services.
- Secure Your Wallets: Use cold storage or hardware wallets for large transactions, update software regularly, and set strong, unique passwords.
- Encrypt Communications: Use end-to-end encrypted apps like Signal or ProtonMail and avoid public Wi-Fi.
- Verify Counterparties: Conduct thorough KYC checks and validate transaction legitimacy to avoid fraud.
- Enable Strong Authentication: Set up multi-factor authentication and use multi-signature wallets for added protection.
- Limit Data Sharing: Share only necessary information and stay compliant with regulations like FinCEN and FATF guidelines.
- Monitor Transactions: Use real-time tools to track suspicious activity and prepare an incident response plan.
- Leverage Privacy Tools: Utilize technologies like Zero-Knowledge Proofs (ZKPs) and secure platforms with robust privacy features.
In OTC crypto trading, you are your own bank. Following these steps minimizes risks and ensures your assets and data remain secure.
8 Essential Security Practices for OTC Crypto Trading
Risks and Security Measures in OTC Crypto Trading
Partner with Trusted OTC Providers
When it comes to secure OTC trading, everything starts with picking the right partner. Reliable OTC providers take the time to carefully vet both buyers and sellers, helping to reduce risks like fraud and defaults. This step is crucial and lays the groundwork for thoroughly assessing a provider’s qualifications.
The stakes couldn’t be higher – over $15 billion has been lost to exchange hacks in just eight years. As Evolve Security warns:
If an authorized user is able to get access to your holdings, you cannot recover the money.
Verify Provider Credentials
Before committing to any OTC provider, it’s essential to evaluate their credentials. Check their track record, licensing, and security measures. Top-tier providers stick to strict Know Your Customer (KYC) and Anti-Money Laundering (AML) standards, ensuring transparency and compliance with legal obligations.
Focus on providers licensed and regulated in well-regarded jurisdictions. For instance, Gemini Trust Company operates under the oversight of the NYDFS and boasts SOC-2 Type II compliant infrastructure.
Also, find out if the provider uses escrow services or third-party custodians to protect funds during transactions. Look for fair fees, a diverse range of supported assets, and a history of successful trades. As BlockchainX puts it:
Security is not a feature, but the cornerstone to any successful OTC crypto exchange.
In addition to verifying credentials, tapping into industry networks can further enhance the safety of your trades.
Use Industry Connections
Trading OTC without leveraging industry connections can leave you exposed to unnecessary risks. Agencies specializing in connecting clients with vetted OTC desks offer access to trusted liquidity providers and institutional investors. These networks provide multiple layers of security that are difficult to establish on your own.
Take BeyondOTC, for example. They connect clients with pre-vetted OTC desks, institutional investors, and liquidity providers. Their network is designed with risk management in mind, including measures to block orders exceeding credit limits and constant monitoring for suspicious activity. Plus, working with such networks often comes with added perks like dedicated account managers, expert support teams, and around-the-clock trading coverage.
Implement Secure Wallet Practices
Securing your digital wallet is crucial – it’s the gateway to your crypto assets. By taking the right precautions, you can significantly reduce the risk of losing funds to hacks or other vulnerabilities.
Use Hardware Wallets or Cold Storage
When handling high-value OTC trades, cold storage is your safest option. By keeping funds offline, you eliminate the risks associated with Web3 interactions. As Kaspersky notes:
Because they operate completely offline and do not have Web3 interaction, cold wallets are considered the most secure type of crypto wallet.
Hardware wallets like the Ledger Nano X and Trezor Model T add an extra layer of protection with features like PIN codes and recovery phrases. However, since they can interact with Web3, they’re not completely risk-free. Cold wallets, on the other hand, avoid these risks entirely by staying offline.
For corporate accounts, it’s critical to ensure that only one authorized individual has access to the private keys of any hardware wallet. And don’t overlook setting up a recovery phrase – it’s your lifeline if the wallet becomes inaccessible.
Update Wallet Security Regularly
Keeping your wallet secure isn’t a one-and-done task. Regular updates to wallet software, firmware, and related systems are vital for patching vulnerabilities as they arise.
Strengthen your login credentials by using unique, complex passwords for all crypto-related accounts and updating them frequently. Open-source wallet software benefits from continuous testing and frequent security patches, making it a reliable option. For institutional traders, implementing a routine review of risk management protocols – preferably at least once a year – can help identify and address potential vulnerabilities.
Use Encrypted Communication Channels
When it comes to OTC trade discussions, the risks of unencrypted communication are too high to ignore. Leaving sensitive details exposed can make you an easy target for attackers.
Use End-to-End Encryption
End-to-end encryption (E2EE) is a must-have for OTC trading discussions. It ensures that only you and your intended recipient can access the messages – keeping prying eyes out.
For secure conversations, rely on encrypted apps like Signal or Session. When it comes to email, opt for services like ProtonMail or Tutanota, and consider using aliases for added privacy.
Corporate accounts should use encryption protocols like PGP or RSA and verify that all communications are secured with HTTPS/SSL. For inter-system data transfers, enforce TLS with modern cipher suites and implement mTLS where applicable.
One crucial rule: never share private keys over messaging apps. It’s a risk not worth taking.
Avoid Public Wi-Fi During Transactions
Public Wi-Fi networks are a hacker’s playground, making them dangerous for high-value transactions. These networks are susceptible to man-in-the-middle attacks, where attackers intercept and manipulate your communications.
Instead of using public Wi-Fi, stick to secure private networks or a no-log VPN like Mullvad or ProtonVPN.
The consequences of weak communication security are real. Consider this: a U.S. investor once lost $24 million when hackers exploited vulnerabilities to take over their phone number and reset exchange logins. While this wasn’t directly linked to public Wi-Fi, it highlights how crucial secure communication is in protecting your assets.
Conduct Due Diligence and Verification
After securing a trustworthy provider and implementing strong wallet practices, the next step in strengthening your OTC trading strategy is thorough due diligence on counterparties and transactions.
In the OTC trading world, verifying counterparties is not just a recommendation – it’s essential. These high-value transactions are prime targets for fraud, and since crypto transfers are irreversible, there’s no fallback if something goes wrong.
Verify Counterparty Identity
The first layer of protection against fraudulent activities is Know Your Customer (KYC) procedures. Reputable OTC desks rigorously screen all participants to ensure they are reliable, reducing risks of fraud or defaults. Both parties involved in the trade undergo KYC and Anti-Money Laundering (AML) checks.
This process typically involves submitting documentation such as government-issued IDs, proof of address, and – for corporate entities – details about authorized signatories and the source of funds. Additional measures may include liveness checks, risk scoring, and enhanced due diligence (EDD). Some platforms even adhere to strict regulatory guidelines to maintain compliance.
When selecting an OTC platform or counterparty, prioritize those with a strong track record in KYC/AML compliance and a history of legitimate transactions. A consistent diligence process for all crypto-related entities not only ensures smoother operations but also mitigates potential regulatory or audit-related risks.
Validate Transaction Legitimacy
Verifying identities is just one part of the equation. It’s equally important to ensure the transaction itself is legitimate. Financial institutions are increasingly requiring crypto wallet screenings before approving funds from crypto trading activities. Using verification tools to screen wallet addresses and transaction histories can help identify and minimize fraud risks in large trades.
Proper verification also confirms that only authorized parties have control over private keys. This is critical, given the irreversible nature of cryptocurrency transactions once they are confirmed. Conducting a detailed review of both the counterparty’s identity and reputation is a key step in safeguarding high-value trades. These practices, when combined, form an integral part of a broader security strategy.
sbb-itb-7e716c2
Enable Multi-Factor and Multi-Signature Authentication
After conducting thorough due diligence, strengthening account security with advanced authentication methods is a crucial next step. These additional layers of protection help secure your accounts and funds against unauthorized access.
Set Up Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA), often called 2FA, adds an extra layer of security beyond just using passwords. Considering that weak or reused passwords are linked to over 25% of data breaches, enabling MFA for both account logins and asset transfers is a must. Hardware-based authentication tools, like YubiKey, are highly recommended. These devices connect via USB and provide cryptographic proof of identity, offering strong defenses against phishing, man-in-the-middle attacks, and replay attacks.
If hardware keys aren’t feasible, authenticator apps like Authy or Google Authenticator are reliable alternatives. These apps use QR codes to generate time-sensitive codes that refresh every 60 seconds. However, avoid relying on SMS-based codes, as they are vulnerable to SIM-swap attacks.
Use Multi-Signature Wallets
Multi-signature (multi-sig) wallets add another layer of security by requiring multiple approvals before any transaction can be executed. This approach significantly reduces the risk of theft, especially for large OTC transactions that involve multiple stakeholders. For businesses managing crypto reserves, multi-sig wallets are a key tool for safeguarding assets in cold storage. They ensure that funds can only be accessed with authorization from several parties.
Minimize Data Sharing and Ensure Regulatory Compliance
When it comes to protecting your data in OTC trading, the key lies in balancing privacy with legal requirements. OTC transactions are designed to maintain confidentiality, but achieving this requires limiting data sharing and adhering to strict regulatory standards.
Share Data on a Need-to-Know Basis
Only share the bare minimum when it comes to transaction details. Avoid discussing your trading strategies publicly or with untrusted parties. To further safeguard your privacy, consider creating a separate crypto identity – complete with unique usernames and a dedicated email address for trading purposes. And remember, keeping your holdings off social media is a smart move.
When working with OTC providers, be mindful of the personal information they can access. Review their permissions and make adjustments as needed. Look for OTC desks that prioritize confidentiality by using strong encryption and enforcing strict internal policies. You can also protect your data by entering confidentiality agreements and exploring non-custodial solutions, which give you more control over your assets and associated information.
Stay Current on Regulations
While limiting data sharing is critical for privacy, staying compliant with regulations is equally important. In the U.S., OTC crypto platforms must follow guidelines from agencies like FinCEN, the SEC, the CFTC, and the IRS. This involves completing KYC checks, which require you to provide proof of identity, address, authorized signatory information, and the source of your funds.
For instance, FinCEN mandates that cryptocurrency businesses file Currency Transaction Reports (CTRs) for transactions over $10,000 and submit Suspicious Activity Reports (SARs) for unusual activities within 30 days. On an international level, the FATF Travel Rule requires Virtual Asset Service Providers to share verified sender and recipient information for qualifying transactions, making robust KYC processes non-negotiable. Reputable OTC desks enforce strict KYC/AML practices to meet these legal obligations. Staying informed about regulatory updates and partnering with providers who prioritize compliance can help you protect both your privacy and your legal standing.
Monitor Transactions and Address Common Risks
After establishing strong authentication and due diligence practices, the next critical step is to continuously monitor transactions. Real-time tracking with Know Your Transaction (KYT) systems adds another layer of protection. These tools analyze data from blockchain networks, wallets, and exchanges to score transactions based on factors like size, source, and destination. If something seems unusual, they send out immediate alerts, helping you detect threats early, prevent fraud, and maintain regulatory compliance.
Use Real-Time Transaction Monitoring
Real-time monitoring allows you to track both direct and indirect exposures by flagging funds tied to darknet markets, sanctioned entities, or known scammers. Advanced tools can trace intermediary addresses, giving you a clear view of the entire transaction chain. Be on the lookout for warning signs such as multiple transactions just under $10,000 (a tactic known as payment structuring) or sudden, unexplained spikes in activity. Similarly, unidentified counterparties that interact with multiple users can also signal potential risks.
For transactions exceeding $10,000, you’ll need to file Currency Transaction Reports (CTRs). The Travel Rule, which applies to transactions of $3,000 or more, requires identifying both the sender and the recipient and sharing this information with the counterparty Virtual Asset Service Provider. If a transaction raises enough red flags to prompt internal action – such as contacting the customer, freezing funds, or restricting activity – you must file a Suspicious Activity Report (SAR) with FinCEN within 30 days.
Prepare an Incident Response Plan
Having a clear, actionable response plan for suspicious activity is essential. This plan should outline risk-based procedures, including steps for contacting customers, freezing funds, or restricting transactions. It’s also crucial to establish notification protocols for surveillance teams and implement controls to prevent orders that exceed pre-set credit limits or indicate duplicate entries.
Incorporating AI and machine learning into your monitoring systems can make a big difference, allowing you to quickly detect and adapt to more advanced fraud schemes. Additionally, the CEO or an equivalent officer should certify compliance annually, and regular reviews of your risk management controls are a must. By layering multiple security measures, you create a robust defense system that can catch and address issues early. These protocols work hand-in-hand with earlier safeguards to build a well-rounded security framework.
Use Privacy-Enhancing Technologies
When it comes to securing OTC crypto trading, Privacy-Enhancing Technologies (PETs) play a key role in complementing wallet security, encrypted communication, and real-time monitoring. These tools help verify, analyze, and collaborate securely without exposing sensitive information. Technologies like Zero-Knowledge Proofs (ZKPs) are particularly valuable for protecting transaction history. Leveraging blockchain privacy features alongside PETs can further secure sensitive trade data.
Use Blockchain Privacy Features
Zero-Knowledge Proofs allow you to confirm that a transaction is valid or compliant without revealing the underlying details. This is especially useful in OTC trades, where verifying counterparty credentials or transaction legitimacy can be done without sharing confidential information.
Secure Multiparty Computation (SMPC) takes collaborative verification to another level. It allows multiple parties – like financial institutions and law enforcement agencies – to combine data for anti-money laundering (AML) efforts and fraud detection without exposing individual customer records. This means transactions can be analyzed for suspicious activity while keeping unrelated data private. Similarly, Homomorphic Encryption (HE) enables computations directly on encrypted data, ensuring sensitive financial information remains secure throughout the process.
For particularly sensitive OTC deals, privacy-oriented cryptocurrencies such as Monero or Zcash are worth considering. These coins are built with advanced privacy features that conceal transaction details, making them a strong choice for trades requiring maximum discretion.
Choose Secure Trading Platforms
To achieve a fully secure trading environment, advanced privacy tools need to be paired with robust platform features. Encryption methods are essential, but the platform itself must also integrate privacy-focused technologies.
When selecting an OTC platform, look for those that offer tokenization to safeguard payment data, real-time transaction monitoring with alerts for suspicious behavior, and comprehensive audit trails for traceability. Platforms should also implement Role-Based Access Control (RBAC) to restrict data access based on user roles, adhering to the principle of least privilege.
Additionally, platforms should undergo regular security audits and penetration tests conducted by independent cybersecurity firms. Compliance with KYC and AML regulations is non-negotiable. While PETs are powerful, they are most effective when combined with strong privacy programs and transparent software capabilities.
Conclusion
When it comes to OTC crypto trading, adopting a strong, multi-layered security strategy isn’t just a good idea – it’s absolutely essential. In a world where transactions are irreversible and the stakes are high, there’s no room for error. The numbers speak for themselves: over $15 billion has been stolen from crypto exchanges in the past eight years.
As BTCC Academy aptly puts it:
In the cryptocurrency world, you are your own bank. There’s no "forgot password" button for your wallet’s private keys and no helpline to reverse a blockchain transaction. If your crypto is stolen, it’s almost always gone forever.
The upside? Following a layered security approach can significantly reduce your risks. Tools like hardware wallets and multi-factor authentication are critical in defending against online threats, especially when weak passwords account for more than a quarter of all data breaches. Encrypted communication channels ensure your trading discussions stay private, while privacy-focused technologies add another layer of protection for sensitive information.
OTC desks play an important role by vetting counterparties and ensuring regulatory compliance, but at the end of the day, personal accountability is key. Hackers only need one slip-up – whether it’s reusing a password, clicking on a phishing link, or sharing a private key over an unsecured channel – to compromise your assets. And with AI-powered blockchain tracking on the rise, prioritizing privacy-enhancing technologies has never been more important.
By following best practices – like working with trusted providers and monitoring transactions in real time – you can protect your identity, secure your keys, and safeguard your capital. These measures are more than just precautions; they’re the foundation of trust and integrity in the crypto market. In this space, where you essentially act as your own bank, such strategies aren’t optional – they’re critical.
Take these steps seriously to secure your OTC trades and protect your crypto investments.
FAQs
What security measures should I prioritize when selecting an OTC crypto trading provider?
When selecting an OTC crypto provider, it’s crucial to focus on regulatory compliance and risk management. A reliable provider should hold proper licensing in the regions where they operate and strictly adhere to KYC (Know Your Customer) and AML (Anti-Money Laundering) standards to verify all parties involved. Transparency is another key factor – providers should offer real-time access to transaction logs, set clear exposure limits, and maintain audit-ready records. Additionally, safeguards like segregating client funds and conducting regular internal audits can go a long way in reducing risks.
Another critical aspect is technical and operational security. Choose providers that enforce multi-factor authentication (MFA), store private keys in cold or hardware wallets, and implement IP and API whitelisting to control access. Features like end-to-end data encryption, frequent security testing, and a well-defined incident response plan are essential to maintaining a secure environment. For example, BeyondOTC follows these industry best practices, ensuring a safe platform for institutional-grade crypto transactions.
How do multi-signature wallets improve the security of OTC crypto transactions?
Multi-signature (or multi-sig) wallets bring an added layer of security to OTC crypto transactions by requiring multiple parties to approve a transaction before it’s executed. Unlike traditional wallets that depend on a single private key, these wallets demand signatures from several authorized participants, significantly lowering the chances of fraud or unauthorized access.
This approach is particularly useful in OTC trading, where large amounts of money are often at stake. By spreading control across trusted individuals, multi-sig wallets ensure that no single person has the power to compromise the funds, making them a dependable option for safeguarding high-value transactions.
Why is it crucial to use privacy-enhancing technologies in OTC crypto trading?
In the world of OTC crypto trading, safeguarding sensitive transaction details and private keys is a top priority. This is where privacy-enhancing technologies come into play. These tools are designed to protect your data from hacking attempts, data breaches, or any unauthorized exposure of confidential information.
By securing your transactions, you’re not just keeping your financial dealings private – you’re also aligning with regulatory standards. This added layer of protection helps build trust and reinforces security, especially when dealing with high-value trades where vulnerabilities can pose significant risks.