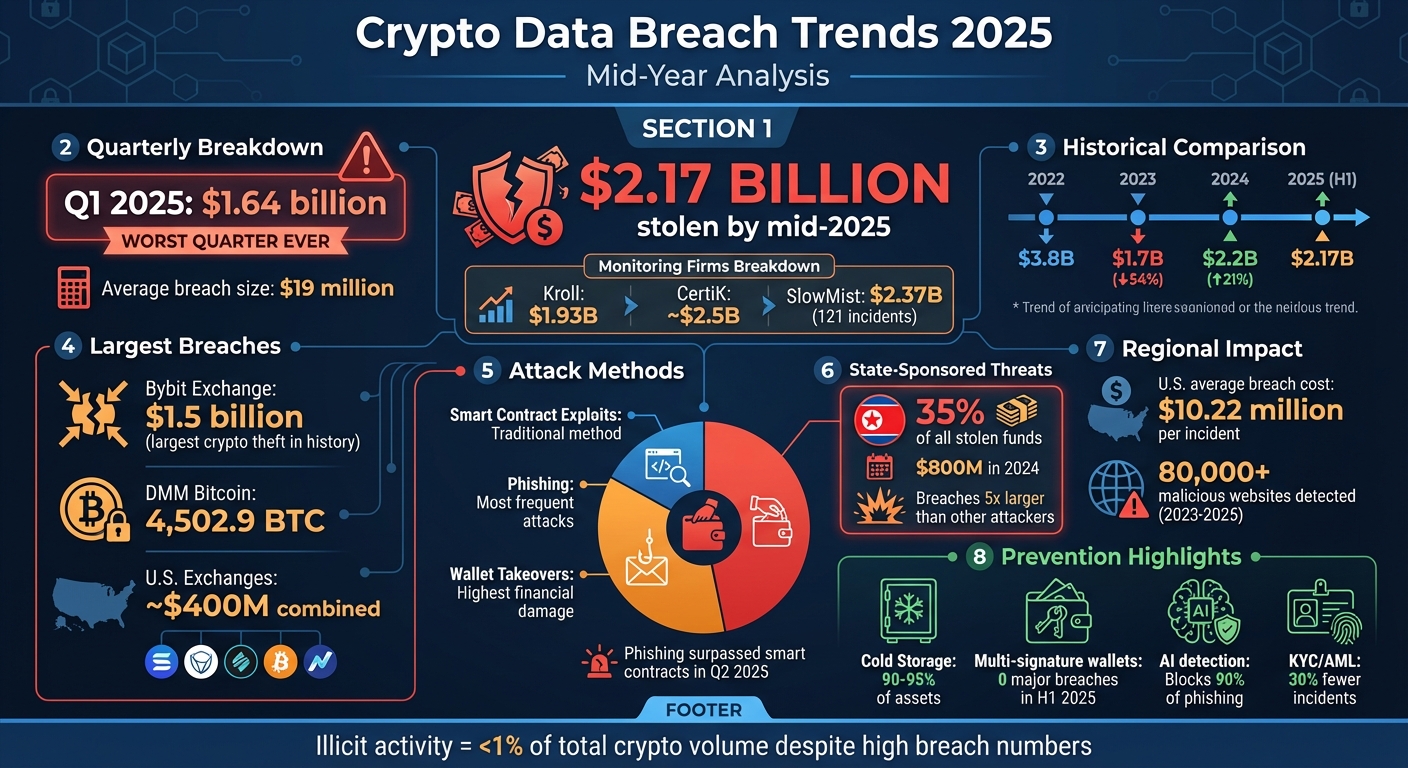
Crypto hacks reached staggering levels in 2025, with $2.17 billion stolen by mid-year alone. The Bybit exchange hack, amounting to $1.5 billion, stands as the largest theft in crypto history. Phishing scams and wallet takeovers are the most common methods, while state-sponsored groups, particularly linked to North Korea, are behind the largest breaches. The U.S. sees the highest average breach costs globally at $10.22 million per incident.
Key insights:
- Q1 2025 losses hit $1.64 billion, the worst quarter on record.
- Wallet takeovers cause the most financial damage, while phishing attacks are the most frequent.
- State-sponsored groups account for 35% of stolen funds, averaging breaches five times larger than other attackers.
- Advanced phishing tactics, including AI-generated content, are becoming harder to detect.
To mitigate risks, crypto platforms must prioritize cold storage, multi-signature wallets, AI-driven phishing detection, and compliance standards like KYC/AML. BeyondOTC and similar partners offer secure solutions by connecting clients with vetted networks and legal safeguards.
2025 Crypto Data Breach Statistics and Attack Methods
Data Breach Statistics and Trends in 2025
2025 Breach Statistics
The numbers for 2025 paint a concerning picture of escalating risks. Monitoring firms have reported losses ranging between $1.93 billion (Kroll) and nearly $2.5 billion (CertiK), with SlowMist documenting approximately $2.37 billion across 121 security incidents by mid-year. These figures highlight the significant financial toll of breaches and set the stage for understanding their broader impact.
Looking at the trends over recent years, the fluctuation in stolen funds underscores the volatility of the industry. In 2022, losses reached $3.8 billion, but this dropped by about 54% to $1.7 billion in 2023. However, 2024 saw a rebound of 21%, with losses climbing to $2.2 billion. In the first half of 2025 alone, SlowMist recorded an average breach size of nearly $19 million, though this figure is heavily influenced by a few massive incidents. Alarmingly, the first quarter of 2025 accounted for $1.64 billion in losses, making it the worst quarter ever for crypto hacks.
Major Breaches and Their Impact
Among the most notable breaches in 2025, the Bybit exchange hack stands out as a landmark event. This single attack disrupted market liquidity and eroded confidence, leading to heightened scrutiny of centralized exchange security practices. It also intensified regulatory discussions around improving custody standards. In response, exchanges across the industry were compelled to reassess their protocols and implement new safeguards.
The DMM Bitcoin attack in 2024 was another significant breach, with hackers stealing 4,502.9 BTC. The stolen funds were funneled through peel chains and cross-chain bridges, forcing the exchange to shut down and compensate affected users. Meanwhile, breaches targeting U.S. exchanges in 2024 and early 2025 caused combined losses of around $400 million, primarily due to credential stuffing, API key theft, and social engineering tactics like account takeovers.
Evolving Attack Methods
Attackers are constantly refining their techniques, making breaches more sophisticated and impactful. Wallet takeovers – where private keys and seed phrases are stolen – have become the leading cause of financial losses, especially for centralized exchanges and custodial wallets. While phishing remains the most common attack method, CertiK’s data from the first half of 2025 shows that wallet takeovers result in the largest financial losses. In Q2 2025, phishing even surpassed traditional smart contract exploits in stolen value. Attackers employed tactics like fake wallet interfaces, malicious browser extensions, and compromised social media accounts to siphon funds.
State-sponsored attacks, however, represent the most severe threat. These operations often involve spear-phishing engineers, compromising build pipelines, and infiltrating key-management systems. The Bybit hack serves as a prime example of this approach – a highly targeted attack on a centralized entity rather than a widespread retail scam. Unlike criminal groups that rely on mass phishing or ransomware, state-sponsored actors focus on long-term reconnaissance, supply-chain compromises, and sophisticated laundering methods. They frequently use complex cross-chain workflows to bypass U.S. and international sanctions enforcement.
Regional and Actor-Specific Analysis
State-Sponsored Cybercrime
North Korea continues to lead the charge in state-backed cybercrime, responsible for a staggering 35% of all stolen cryptocurrency in 2024 – equating to nearly $800 million. Their operations are, on average, five times larger than those of other groups, with a focus on stealing private keys and seed phrases from centralized platforms rather than exploiting smart contract vulnerabilities.
This trend persisted into 2025 with devastating results. A standout example is the $1.5 billion Bybit hack, attributed to North Korean-linked groups. Their approach combines long-term reconnaissance with sophisticated social engineering targeting employees. These tactics have played a major role in driving the sharp increase in crypto thefts during the first half of 2025.
Global Phishing Trends
Beyond state-sponsored attacks, phishing threats have evolved dramatically. Between 2023 and 2025, security analysts flagged over 80,000 malicious or suspicious websites mimicking major exchanges, wallets, and DeFi platforms . Many of these campaigns now use AI-generated content and deepfake customer support agents, making them increasingly difficult to detect.
In early 2025, phishing attacks accounted for the largest share of crypto-related breaches. Data from Q2 shows that phishing surpassed smart contract exploits in terms of total stolen value. The U.S. bore the brunt of these attacks, with average breach losses climbing to $10.22 million per incident. Attackers also tailored phishing campaigns to specific regions, impersonating well-known brands like Binance, Coinbase, and MetaMask to steal user credentials and seed phrases. These developments highlight the growing sophistication of phishing in the crypto space.
Crypto Illicit Activity Trends
The total volume of illicit crypto transactions fell to $45 billion in 2024 – a 24% decline compared to 2023. This drop reflects improvements in blockchain transparency, stricter compliance measures, and more aggressive enforcement. However, while the number of incidents decreased, the financial impact of individual events has grown significantly.
Stronger enforcement in the U.S. and EU has driven money laundering activities toward high-risk exchanges, mixers, and DeFi protocols with weak KYC measures. These platforms often operate in jurisdictions with minimal regulation or under sanctions. Despite the overall reduction in illicit activity, the concentrated nature of these crimes underscores the need for ongoing advancements in security strategies.
Data Breach Prevention Strategies for 2025
Improving Wallet Security
To protect funds, store 90–95% of assets in cold storage, such as hardware wallets or air-gapped systems. This keeps the majority of your holdings offline and less vulnerable to cyberattacks. Hot wallets, on the other hand, should only hold enough funds to cover a few days of operations, like immediate withdrawals or trades. Many major breaches have occurred because private keys were stored on systems connected to the internet.
Another crucial step is to use multi-signature wallets to distribute signing authority. For example, requiring 2-of-3 or 3-of-5 approvals for transactions ensures that no single person, device, or location has full control. Data from the first half of 2025 shows that exchanges implementing multi-signature setups after the losses of 2024 reported zero major wallet compromises. In contrast, single-key wallets accounted for $2.37 billion in stolen funds during the same period.
For private key management, rely on hardware security modules (HSMs) or trusted hardware wallets. Avoid saving seed phrases in cloud-based notes or messaging apps. Instead, store backups in separate, secure locations and document your key management procedures carefully.
Lastly, invest in advanced threat detection tools to combat evolving phishing tactics, which remain a major risk.
Using Advanced Threat Detection
AI-driven phishing detection tools, like Darktrace and Vectra AI, can block up to 90% of phishing attempts by analyzing email patterns, identifying suspicious URLs, and monitoring unusual login behaviors. In early 2025, a major decentralized exchange thwarted a $150 million phishing campaign by quickly detecting deepfake impersonations of executives.
To strengthen your defenses, integrate these tools with your security information and event management (SIEM) platform. This allows for real-time monitoring of anomalies, such as unusual transaction speeds, login locations, and withdrawal patterns. Start by setting thresholds for detecting irregularities in hot wallets, then expand machine-learning capabilities to other endpoints.
While technical measures are essential, pairing them with strong compliance and legal protocols can further reduce breach risks.
Compliance and Legal Safeguards
Implementing rigorous KYC (Know Your Customer) and AML (Anti-Money Laundering) standards can significantly reduce breach risks by keeping bad actors out. In 2025, U.S.-based companies with robust KYC protocols reported 30% fewer security incidents.
Additionally, legal frameworks like SOC 2 audits, GDPR/CCPA compliance, and expert breach response templates can enhance your organization’s ability to respond to incidents effectively. Firms like BeyondOTC connect blockchain projects with experienced legal teams to navigate complex KYC/AML requirements, reducing exposure to state-sponsored threats. Partnering with trusted legal experts also provides access to shared threat intelligence, which can help mitigate mega-breaches. These breaches averaged $375 million in damages during 2024 alone.
sbb-itb-7e716c2
BeyondOTC‘s Role in Security and Networking

Secure OTC Trading Solutions
Cryptocurrency transactions, especially high-volume ones, come with their fair share of risks. BeyondOTC tackles these challenges by connecting clients with carefully vetted OTC desks, institutional investors, and liquidity providers. This rigorous vetting process reduces vulnerabilities such as wallet takeovers and state-sponsored attacks. For instance, the $1.5 billion Bybit incident underscores the importance of robust security measures. BeyondOTC partners implement multi-signature wallets and audited security protocols to help prevent such breaches.
Since its inception, BeyondOTC has facilitated over $250 million in Bitcoin transactions and $30 million in altcoin trades. These transactions are conducted exclusively with partners who adhere to strict security standards. Additionally, their deal room platform ensures that sensitive data is shared securely during exclusive transactions, providing an added layer of protection. This secure infrastructure works hand-in-hand with their legal and compliance protocols, creating a comprehensive safety net for clients.
Legal and Compliance Assistance
In a world where cyber threats continue to evolve, regulatory compliance is more important than ever. BeyondOTC’s Legal Consultancy service connects cryptocurrency projects with blockchain law experts who specialize in key areas such as key management, breach reporting, and KYC/AML standards. This expertise is critical, especially as state-sponsored actors increasingly target private keys with advanced techniques.
BeyondOTC also supports clients in implementing vital legal safeguards, including SOC 2 audits and GDPR/CCPA compliance. Their services extend to establishing incident response protocols that help protect against both regulatory penalties and security vulnerabilities. By leveraging their network of compliance professionals, clients can navigate complex regulations while staying ahead of potential threats.
Networking with Trusted Industry Partners
Security and compliance are crucial, but building strong industry connections is just as important. BeyondOTC’s global network spans over 50 countries, linking clients with verified exchanges, launchpads, and market makers. This extensive network has facilitated over $2 billion in fundraising efforts and $5 billion in total value locked (TVL) solutions.
One of BeyondOTC’s key advantages is acting as a single point of contact, eliminating the risks tied to independently vetting multiple partners. This approach is particularly valuable in light of the 121 security incidents reported in the first half of 2025. By thoroughly vetting their partners, BeyondOTC reduces the likelihood of phishing attacks and service breaches, ensuring that clients engage only with trusted and reliable entities.
North Korea’s 2025 Crypto Thefts Surpass $2 Billion, Bybit Among The Biggest Victims | World News
Conclusion: Managing Data Breach Risks in 2025
By mid-July 2025, crypto hacking losses had reached a staggering $2.17 billion. Of that, $1.64 billion occurred in Q1 alone, with 121 incidents reported in the first half of the year. Despite these numbers, illicit activity made up less than 1% of overall crypto transaction volume.
The contrasting outcomes of Coinbase and Bybit highlight the importance of having strong security measures in place. Coinbase successfully avoided a $20 million extortion attempt by swiftly implementing compliance protocols, preventing any payout. On the other hand, Bybit faced a devastating loss of 401,347 ETH, worth $1.5 billion, after a wallet breach linked to North Korean actors – the largest crypto theft ever recorded. These examples emphasize the need to move from reactive responses to proactive risk management strategies.
State-sponsored threats continue to drive the scale of breaches, underscoring the importance of robust security practices. Effective key management, the use of hardware wallets to counter phishing (the leading cause of incidents by volume), and compliance systems capable of resisting sophisticated attacks are all critical. For instance, in October 2025, the U.S. Department of Justice recovered $15 billion in Bitcoin from a large-scale pig butchering scam, showcasing the role of regulatory efforts in asset recovery.
Addressing these high-stakes risks often requires collaboration with reliable partners. BeyondOTC’s model exemplifies this by connecting clients to trusted OTC desks, legal experts, and verified exchanges in over 50 countries. Their network, which has facilitated over $250 million in Bitcoin transactions and $30 million in altcoin trades, adheres to strict security protocols. This approach minimizes the risks of dealing with unvetted entities and provides a safer framework for managing high-value trades.
To manage breach risks effectively, the industry must integrate advanced technologies, enforce strict compliance, and foster strategic partnerships. While the average cost of a U.S. data breach stands at $10.22 million, investing in tools like multi-signature wallets and AI-driven threat detection offers a more cost-efficient alternative to reactive measures. As institutional adoption of cryptocurrency grows, the focus should remain on vetted access, legal protections, and building trusted networks to maintain confidence in an industry still evolving under intense scrutiny.
FAQs
How can crypto platforms protect users from wallet takeovers and phishing scams?
Crypto platforms can better protect their users by adopting multi-factor authentication (MFA), which adds extra layers of security to account access. This ensures that even if one credential is compromised, additional verification steps are required to gain entry.
Educating users on how to spot phishing attempts – like identifying suspicious emails or links – is another critical step. Platforms should also emphasize the importance of using strong, unique passwords and encourage regular updates to software, which helps address potential vulnerabilities.
To further safeguard sensitive data and assets, advanced tools such as hardware wallets and encryption can be employed. When these measures are prioritized, the chances of wallet takeovers and phishing attacks drop significantly.
How do state-sponsored hacking groups, like those from North Korea, affect the cryptocurrency industry?
State-sponsored hacking groups, including those tied to North Korea, have made a significant mark on the cryptocurrency world. These groups are known for orchestrating massive thefts, often zeroing in on exchanges, wallets, and decentralized finance (DeFi) platforms. The financial toll of these attacks can reach billions of dollars, shaking market stability and eroding trust among investors.
To counter these threats, the crypto industry has stepped up its cybersecurity game. By adopting stricter protocols and deploying advanced defense systems, the sector aims to stay ahead of these sophisticated attackers. These incidents serve as a stark reminder of the need for strong security measures and constant vigilance to protect digital assets and uphold confidence in the ecosystem.
How can crypto exchanges strengthen security and ensure compliance?
To strengthen security and ensure compliance, crypto exchanges need to prioritize several key measures. Implementing Know Your Customer (KYC) and Anti-Money Laundering (AML) protocols is essential for verifying user identities and deterring illegal activities. Adding multi-factor authentication (MFA) provides an extra layer of security for user accounts, while employing advanced encryption techniques protects sensitive information from breaches. Conducting regular security audits helps uncover potential vulnerabilities, and keeping pace with changing regulations ensures legal obligations are met. These combined efforts contribute to a more secure and compliant trading environment.




